2 How it works
SAFR Mobile Credentials users 2 factors to authenticate:
- User’s face
- A trusted Mobile Credential unique to each user
Both factors are required to trigger and Access Granted event. When a person is within 20 feet (7 meters) of SAFR SCAN, their phone will automatically transfer the user’s mobile credential to SAFR SCAN. SAFR SCAN authenticates the Mobile Credential, holds this credential, and monitors for the user’s face. When the user approaches SAFR SCAN and present’s their face, SAFR SCAN authenticates their face and issues an Access Granted event.
SAFR Mobile Credentials are managed by SAFR Key SAFR Key for Android or iOS. SAFR Key creates and stores each user’s Mobile Credential securely on the user’s personal device. Users are prompted to install SAFR Key and create their mobile credential as part of the invitation flow described below.
SAFR Mobile Credentials use the PKOC (Public Key Open Credential) standard. SAFR is interoperable with mobile credentials created by other manufactures. SAFR and SAFR 2.0 Mobile Credentials offer enhanced capability such as embedded PII data.
SAFR Mobile Credentials offers two modes of operation.
-
Distributed Factors – Face and/or access card id are loaded via ethernet.
- Both face and credentials are transferred from the PACS (Physical Access Control System) Software to SAFR Server and transmitted to SCAN over Ethernet.
-
Embedded Factors – Face and/or access card id are loaded into SAFR SCAN via Bluetooth
- Users face image is captured on the phone and transmitted directly to SAFR SCAN via the phone’s Bluetooth only during access transactions.
2.1 SAFR Mobile Credentials with Distributed Factors
2.1.1 Invitation Flow
The diagram below describes the flow for SAFR Mobile Credentials with Distributed Factors.

Users are granted a mobile credential through an invite flow. Before the invite flow, the distributed method requires that face and credentials be copied from the PACS to SAFR Server.
The invite include a link that the user will use to initiate the credential registration. If the user does not already have the SAFR Key App, they will be prompted to install it from the App/Play Store. Once installed, the user can click the link again to create the credential. If enabled, the credential is then transmitted to SAFR Server or SAFR Cloud via the SAFR Cloud bridge. Finally, the credential is synchronized to the person record on SAFR SCAN where it is then ready to use as the 2nd authentication factor.
2.1.2 Authentication Flow
Below figure shows the authentication flow.

As long as the SAFR Key application is allowed to run in the in the background, the user’s Mobile Credential is automatically transmitted to SAFR SCAN when in range. The user then only need to present their face which signals intention and the user’s access card credentials are sent to the control panel.
2.2 SAFR Mobile Credentials with Embedded Factors
The diagram below describes the flow for SAFR Mobile Credentials with Embedded Factors.

The flow is similar to Distributed except that card number is encrypted into the invite and face is collected on the user’s mobile phone and stays there along with the card number. The mobile credential (without embedded factors) can still be transmitted back to the user records if desired.
2.2.1 Authentication Flow
Below figure shows the authentication flow.

Works much the same way as Distributed but mobile credential includes face and optionally the card number.
2.3 Mobile Credential QuickStart
Following describes how to get started right away with SAFR Mobile Credentials.
Either in SAFR Desktop or SAFR Server Web Console, Enable SAFR Cloud Connect as follows:
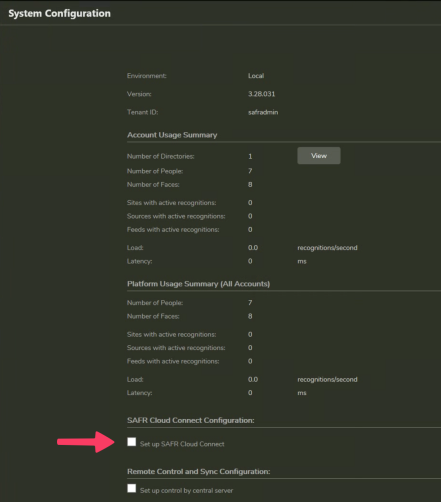
- Open SAFR Desktop > Tools menu > System Configuration (or open http://localhost:8090/status)
-
Scroll down to SAFR Cloud Connect Configuration
-
Check “Set up SAFR Cloud Connect”.
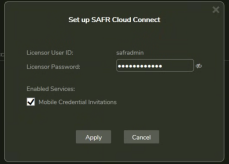
- Enter Licensor password and check “Mobile Credential Invitations”
Either in SAFR Desktop or SAFR SCAN Web Console, perform following:
-
Set Access Mode in Operation > Access Control as follows:

-
Enable SAFR Mobile Credentials in System > Mobile Credentials

-
Configure as follows:
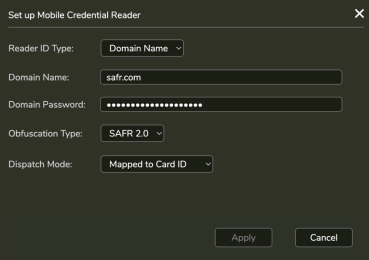
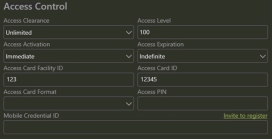
- Open Person Record send invite
|
Click “Invite to register” |
Complete as follows: |
|
|
|
- An email will be opened with invitation link. Click “Send”.
-
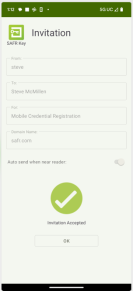
Open the email on Android or iOS phone, click the link and click Accept.
If prompted, accept Android/iOS Location and Nearby Devices permissions.
|
Accept Invite |
Snap Photo |
Review Photo |
Invite Accepted |
|
|
|
|
|
2.4 SAFR Key Application
2.4.1 Background Operation
SAFR Key application can be granted permission to run in the background. This occurs shortly after installation. The user is prompted to allow SAFR Key to access device Bluetooth either while the app is running or always. If always granted, SAFR Key will automatically interact with SAFR SCAN device when in range (about 15 to 20 feet or 5 to 7 meters).
2.4.1.1 About Android Phones
Not all Android phones operate the same. While most Android phones will run continuously in the background, some will turn off the Bluetooth receiver and require that the phone be activated in order to turn this Bluetooth receiver on. For phones like this, SAFR SCAN will not automatically detect the reader and transmit its credentials until turned on. While the user does not need to unlock the phone, they need to wake the phone in the manufacturer’s specific method such as pressing power button or tapping the screen.